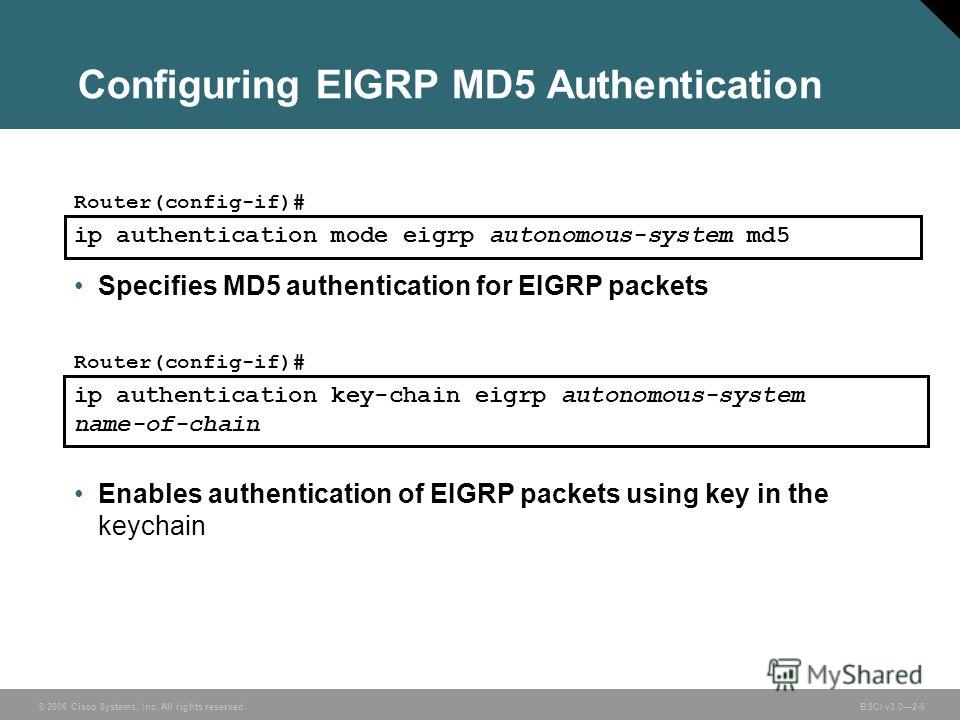
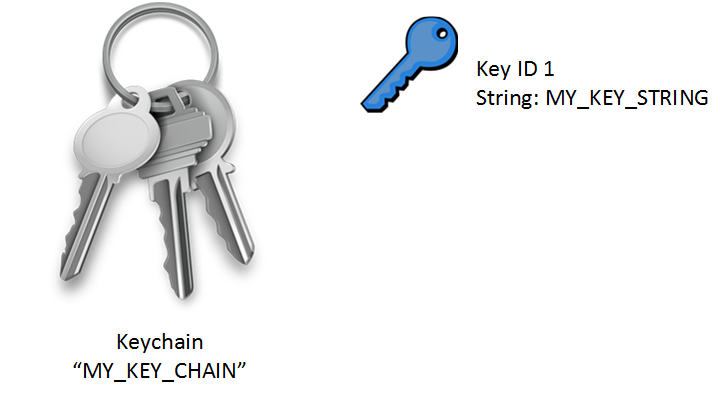
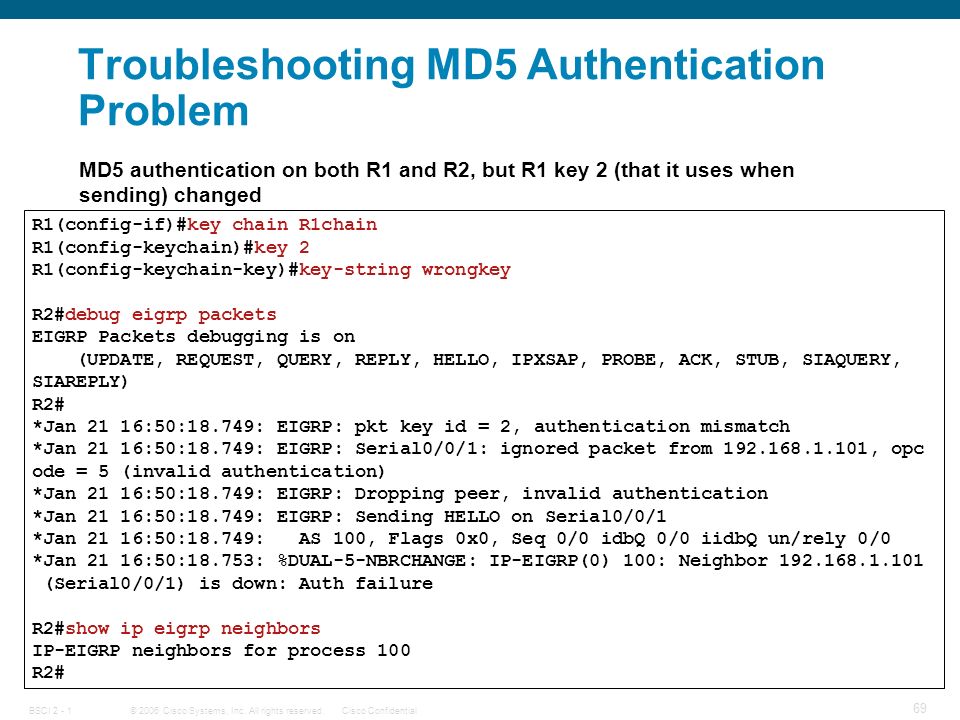
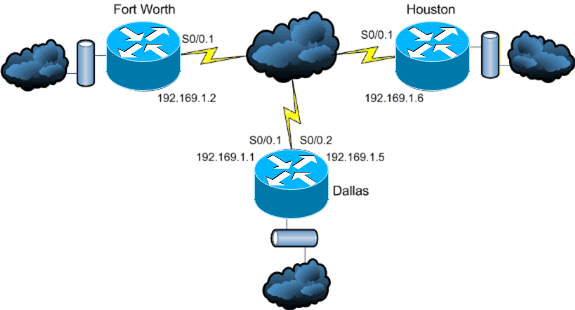
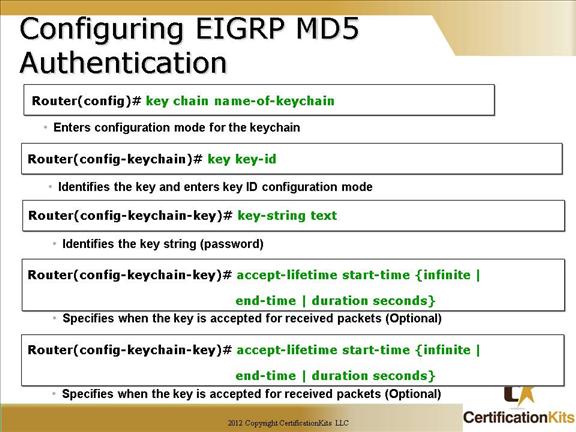
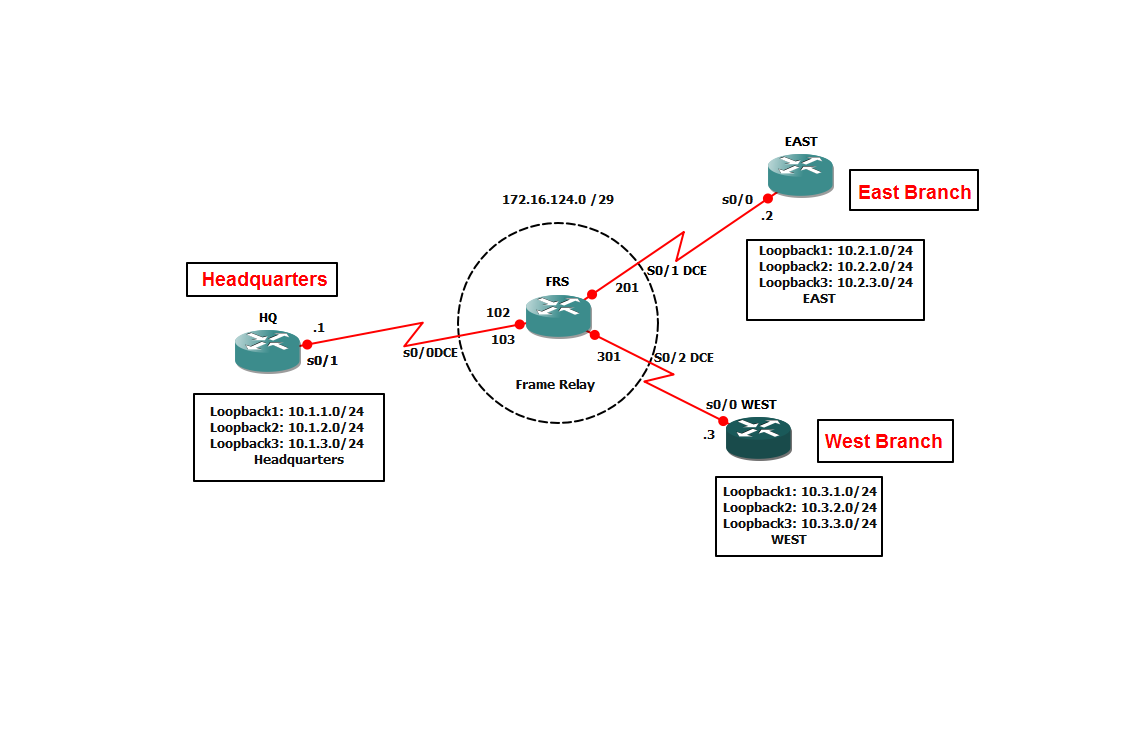
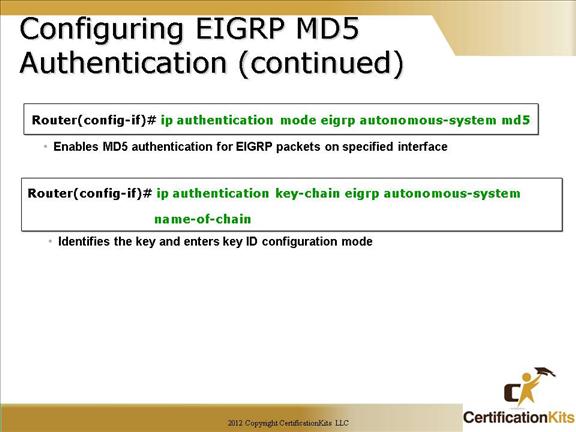
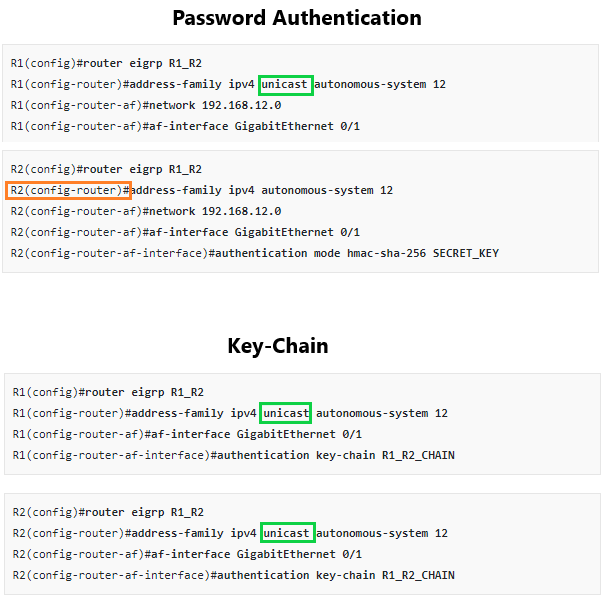
Which key chain is being used for authentication of EIGRP adjacency between R4 and R2? Answer in Here
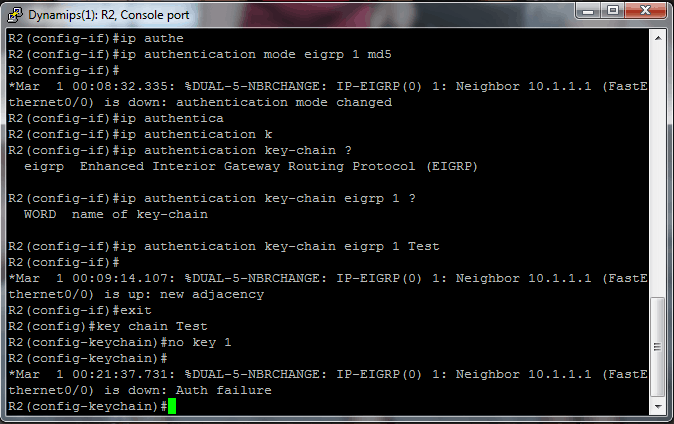
Cisco EIGRP authentication – what is the key? | Interface Technical Training | Interface Technical Training

15.2 EIGRP Authentication Configuration Checklist – Stuck-in-Active: Journal of an IT-Network Administrator

Which of the following key strings will RouterB use when sending EIGRP packets? (Select the best answer.) - ICT Community
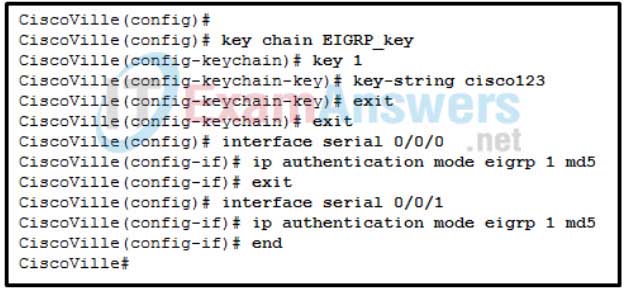
Refer to the exhibit. Router CiscoVille has been partially configured for EIGRP authentication. What is missing that would allow successful authentication between EIGRP neighbors?

Cisco.300-101.v2020-01-06.q78/No.77: You have been asked to evaluate how EIGRP is functioning in a customer network. (Exhibit) Which key chain