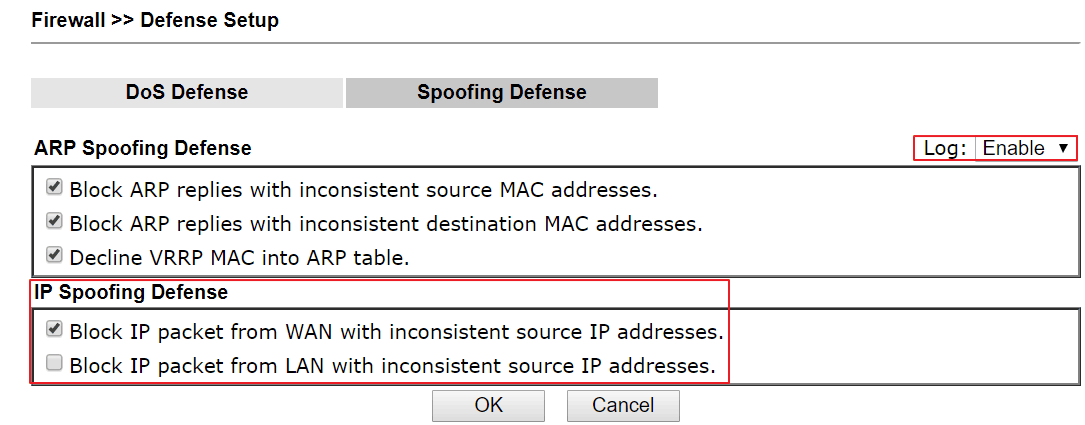
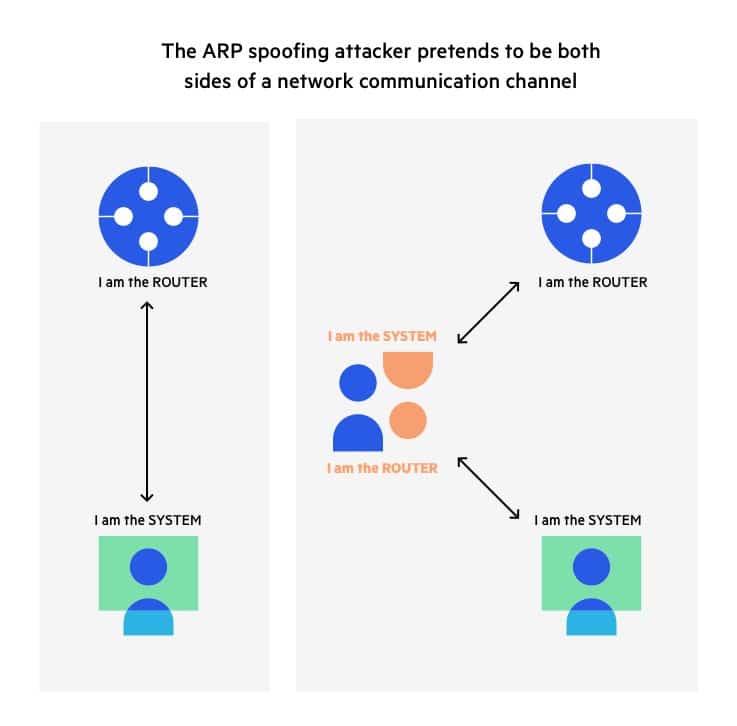
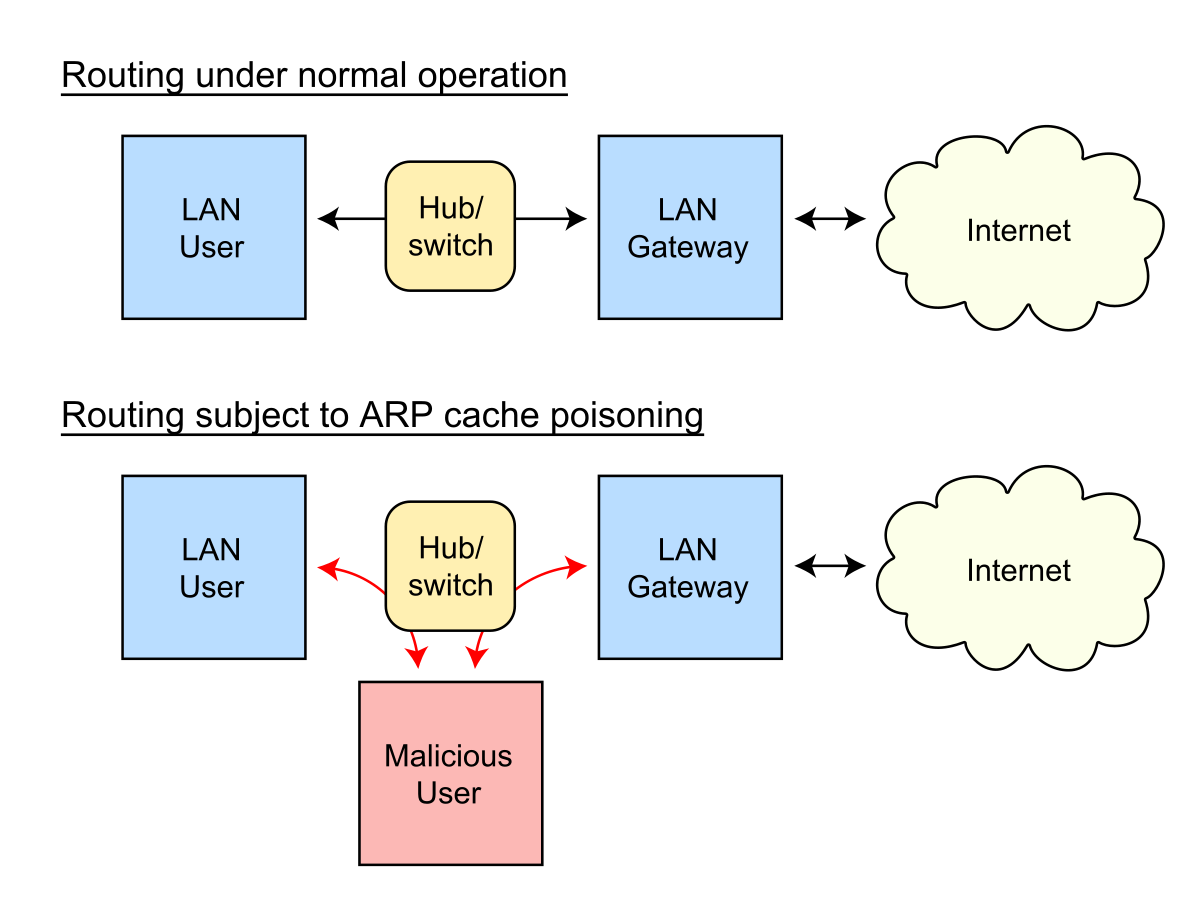
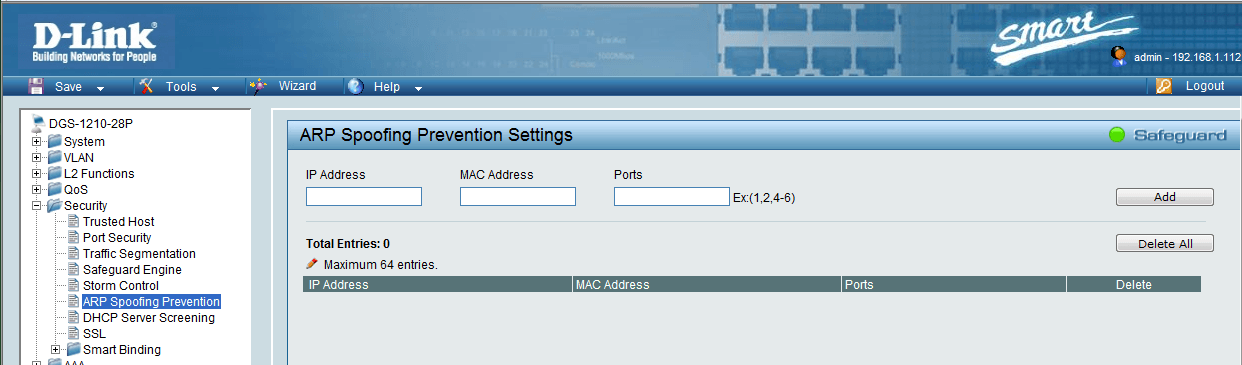
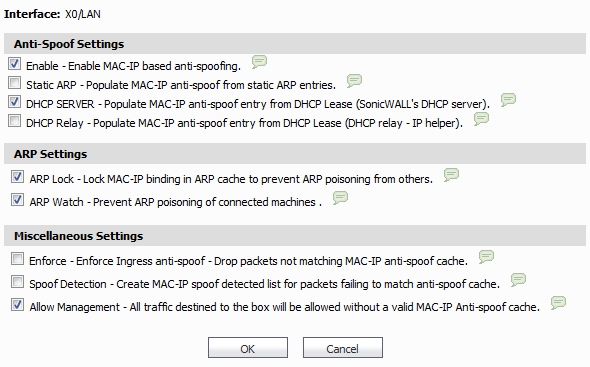
CYSTACK - ARP Spoofing: ARP Spoofing is an attack in which an attacker can send falsified ARP messages over a local area network and link the victim's IP address with his MAC

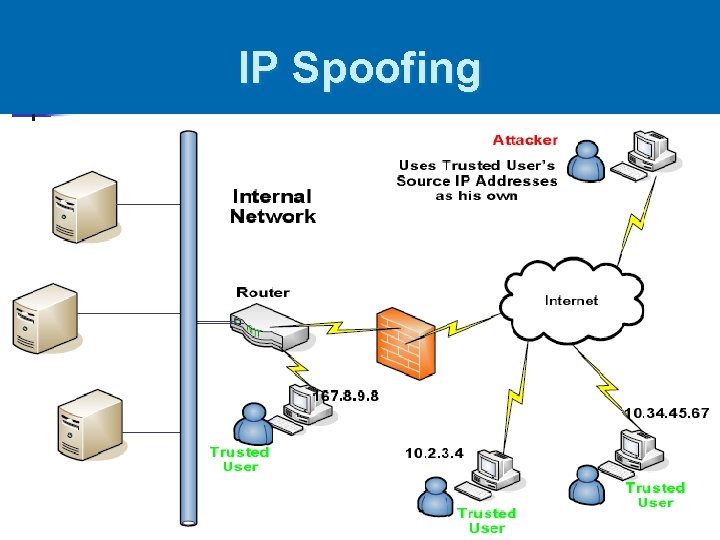
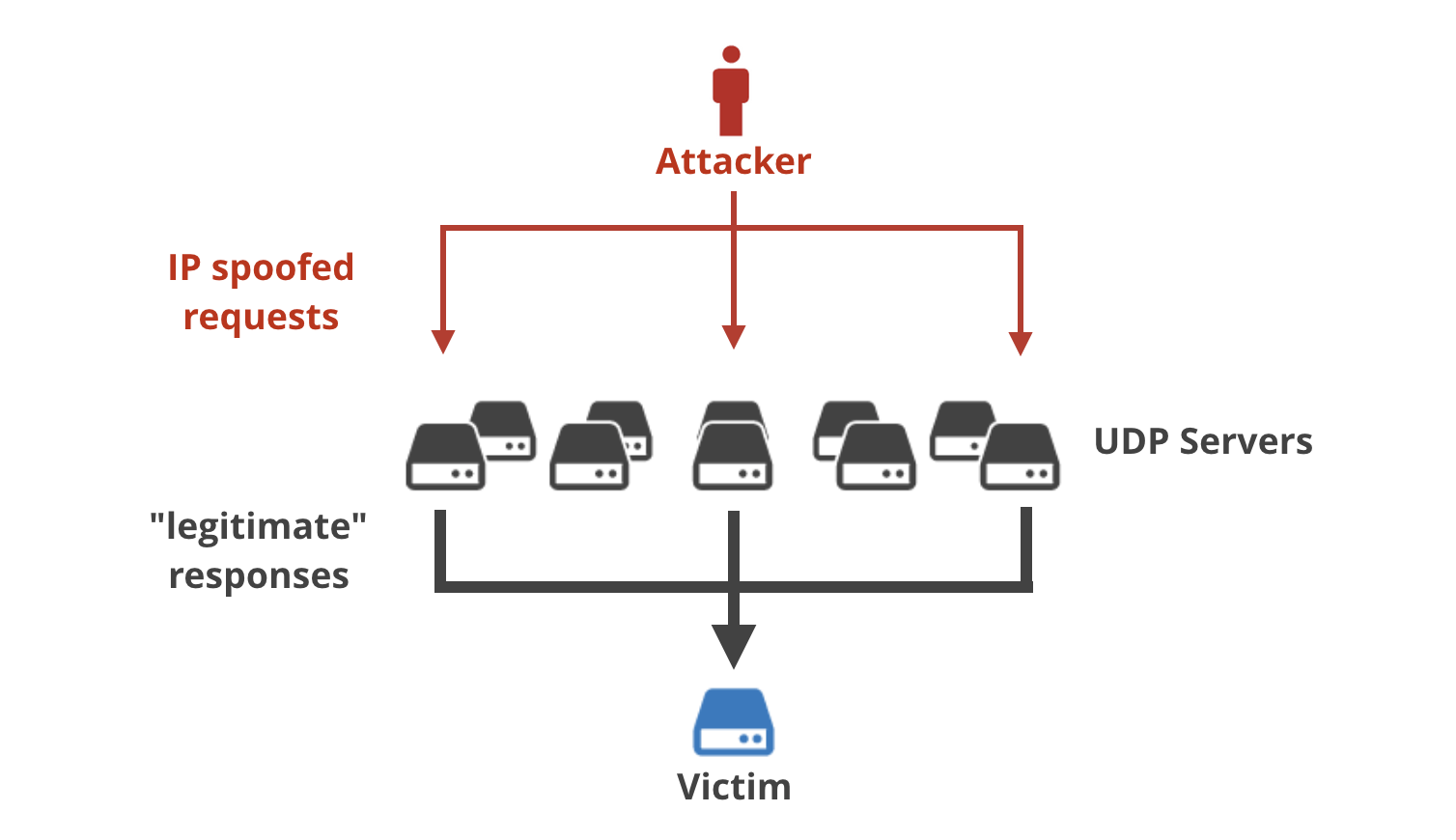
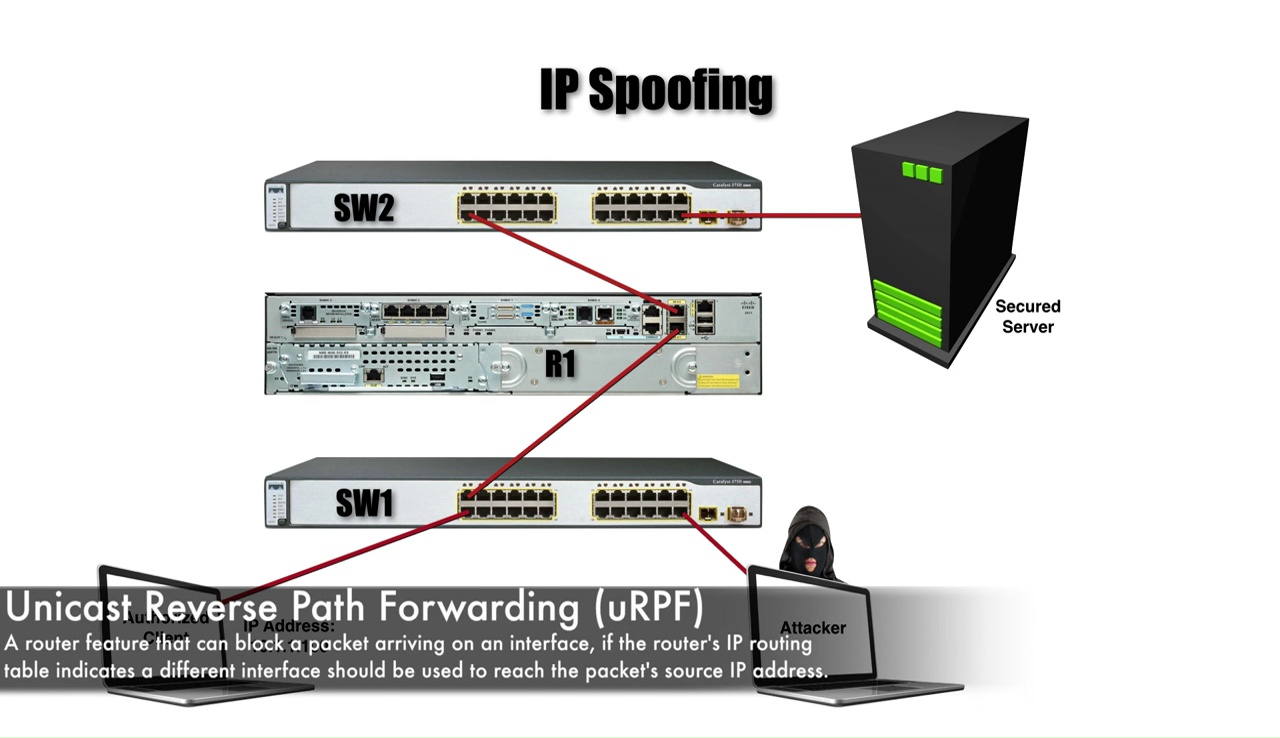
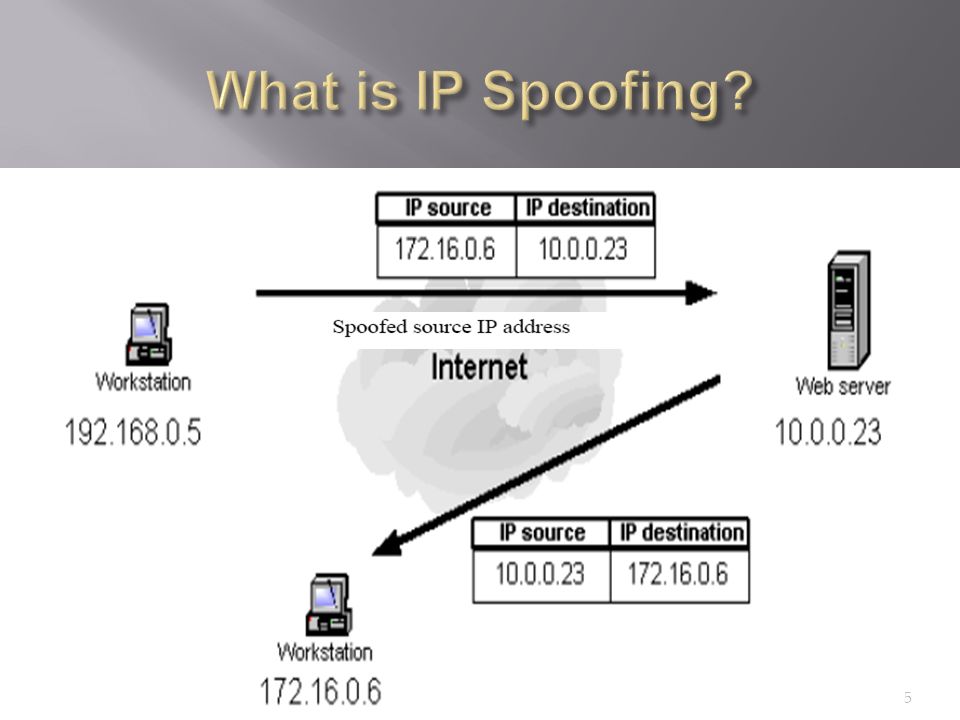
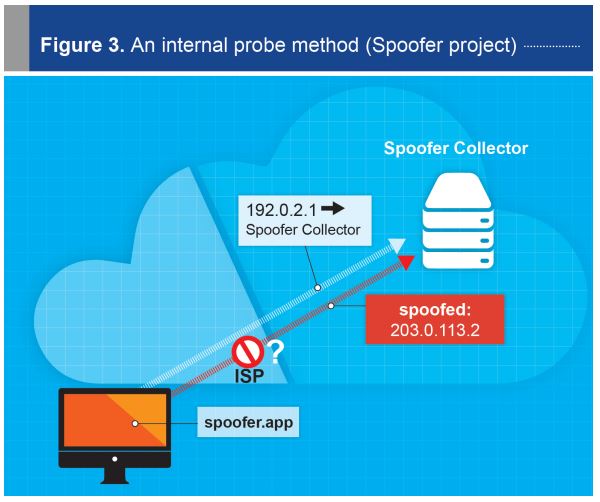
IP Spoofing. The figure shows how the attacker spoofs the source field... | Download Scientific Diagram